2022年の振り返りとしてやったことをまとめる。
目標管理
例年通り、四半期ごとの見直し、月次の進捗確認で運用をした。 1,4,7,10月に目標の見直しを行い次四半期の目標を立て、2,3,5,6,8,9,11,12月は進捗を確認する運用。
大項目として以下4つを設け、それぞれ中項目の目標を立てた。中項目をさらに細分化して、四半期ごとに小項目での目標管理をした。括弧内は中項目のうち、達成できた数を記載。
- 読書(2/3)
- 健康(1/2)
- 英語(1/1)
- 趣味(2/5)
論文
1月
Amin, K., Dick, T., Kulesza, A., Medina, A. M., & Vassilvitskii, S. (2019). Differentially private covariance estimation. Advances in Neural Information Processing Systems, 32(NeurIPS).
Stadler, T., Oprisanu, B., & Troncoso, C. (2020). Synthetic Data -- Anonymisation Groundhog Day.
Rogers, R., Subramaniam, S., Peng, S., Durfee, D., Lee, S., Kancha, S. K., Sahay, S., & Ahammad, P. (2020). LinkedIn’s Audience Engagements API: A Privacy Preserving Data Analytics System at Scale. http://arxiv.org/abs/2002.05839
2月
- Cao, Yang and Yoshikawa, Masatoshi and Xiao, Yonghui and Xiong, Li, Quantifying differential privacy under temporal correlations, Data Engineering (ICDE), 2017 IEEE 33rd International Conference on, 821--832, 2017.
3月
- Kareem Amin, Jennifer Gillenwater, Matthew Joseph, Alex Kulesza, Sergei Vassilvitskii. "Plume: Differential Privacy at Scale" arXiv preprint arXiv:2201.11603 (2022).
4月
- Cangialosi, Frank, et al. "Privid: Practical, privacy-preserving video analytics queries." arXiv preprint arXiv:2106.12083 (2021). https://www.usenix.org/system/files/nsdi22-paper-cangialosi.pdf
5月
- Chaudhuri, Kamalika, Jacob Imola, and Ashwin Machanavajjhala. "Capacity bounded differential privacy." Advances in Neural Information Processing Systems 32 (2019). https://proceedings.neurips.cc/paper/2019/file/04df4d434d481c5bb723be1b6df1ee65-Paper.pdf
6月
Adam, Nabil R., and John C. Worthmann. "Security-control methods for statistical databases: a comparative study." ACM Computing Surveys (CSUR) 21.4 (1989): 515-556. https://dl.acm.org/doi/pdf/10.1145/76894.76895
Rowe, Neil C. "Diophantine inferences from statistical aggregates on few-valued attributes." 1984 IEEE First International Conference on Data Engineering. IEEE, 1984.
7月
Denning, Dorothy Elizabeth Robling. Cryptography and data security. Vol. 112. Reading: Addison-Wesley, 1982. https://core.ac.uk/download/pdf/36729637.pdf (6.1-6.4)
Matsumoto, Marin, et al. "Measuring Lower Bounds of Local Differential Privacy via Adversary Instantiations in Federated Learning." arXiv preprint arXiv:2206.09122 (2022). https://arxiv.org/pdf/2206.09122.pdf
Dwork, Cynthia, Nitin Kohli, and Deirdre Mulligan. "Differential privacy in practice: Expose your epsilons!." Journal of Privacy and Confidentiality 9.2 (2019). https://par.nsf.gov/servlets/purl/10217360
9月 - Kifer, Daniel, and Ashwin Machanavajjhala. "No free lunch in data privacy." Proceedings of the 2011 ACM SIGMOD International Conference on Management of data. 2011. https://www.cse.psu.edu/~duk17/papers/nflprivacy.pdf
12月 - El Emam, Khaled, et al. "A systematic review of re-identification attacks on health data." PloS one 6.12 (2011): e28071. https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0028071
ざっと読み、抜粋読み
1月
- Desfontaines, D., Voss, J., Gipson, B., & Mandayam, C. (2022). Differentially private partition selection. Proceedings on Privacy Enhancing Technologies, 2022(1), 339–352. https://doi.org/10.2478/popets-2022-0017
3月
- Asi, Hilal, John Duchi, and Omid Javidbakht. "Element level differential privacy: The right granularity of privacy." arXiv preprint arXiv:1912.04042 (2019).
4月
bo Wang, Hongtao Li, Yina Guo, Xiaoyu Ren, "An Ecient Location Privacy Protection Method for Location-Based Services based on Differential Privacy", Research Square, 2022 . https://assets.researchsquare.com/files/rs-1504387/v1_covered.pdf?c=1649083710
Gorka Abad, Stjepan Picek, V´ıctor Julio Ram´ırez-Dur´an, Aitor Urbieta, "On the Security & Privacy in Federated Learning". arXiv preprint arXiv:2112.05423 (2022). https://arxiv.org/pdf/2112.05423.pdf
Yeom, Samuel, et al. "Privacy risk in machine learning: Analyzing the connection to overfitting." 2018 IEEE 31st computer security foundations symposium (CSF). IEEE, 2018. https://arxiv.org/pdf/1709.01604.pdf
Song, Liwei, and Prateek Mittal. "Systematic evaluation of privacy risks of machine learning models." 30th USENIX Security Symposium (USENIX Security 21). 2021. https://www.usenix.org/system/files/sec21-song.pdf
Nasr, Milad, Reza Shokri, and Amir Houmansadr. "Comprehensive privacy analysis of deep learning: Passive and active white-box inference attacks against centralized and federated learning." 2019 IEEE symposium on security and privacy (SP). IEEE, 2019. https://www.comp.nus.edu.sg/~reza/files/Shokri-SP2019.pdf
Shokri, Reza, et al. "Quantifying location privacy." 2011 IEEE symposium on security and privacy. IEEE, 2011. https://orca.cardiff.ac.uk/37912/1/Quantifying_Location_Privacy.pdf
Ateniese, Giuseppe, et al. "Hacking smart machines with smarter ones: How to extract meaningful data from machine learning classifiers." International Journal of Security and Networks 10.3 (2015): 137-150. https://arxiv.org/pdf/1306.4447.pdf
Murakonda, Sasi Kumar, and Reza Shokri. "Ml privacy meter: Aiding regulatory compliance by quantifying the privacy risks of machine learning." arXiv preprint arXiv:2007.09339 (2020). https://arxiv.org/pdf/2007.09339.pdf
Tseng, Wei-Cheng, Wei-Tsung Kao, and Hung-yi Lee. "Membership Inference Attacks Against Self-supervised Speech Models." arXiv preprint arXiv:2111.05113 (2021).
5月
Tramèr, Florian, et al. "Stealing Machine Learning Models via Prediction {APIs}." 25th USENIX security symposium (USENIX Security 16). 2016. https://www.usenix.org/system/files/conference/usenixsecurity16/sec16_paper_tramer.pdf
Salem, Ahmed, et al. "Ml-leaks: Model and data independent membership inference attacks and defenses on machine learning models." arXiv preprint arXiv:1806.01246 (2018). https://arxiv.org/pdf/1806.01246.pdf
Lindell, Yehuda, and Benny Pinkas. "Privacy preserving data mining." Journal of cryptology 15.3 (2002). https://link.springer.com/content/pdf/10.1007/s00145-001-0019-2.pdf
Canny, John. "Collaborative filtering with privacy via factor analysis." Proceedings of the 25th annual international ACM SIGIR conference on Research and development in information retrieval. 2002. https://www.researchgate.net/profile/John-Canny/publication/3948694_Collaborative_Filtering_with_Privacy/links/5581e03708ae6cf036c16ff4/Collaborative-Filtering-with-Privacy.pdf
Stewart, Kathy A., and Albert H. Segars. "An empirical examination of the concern for information privacy instrument." Information systems research 13.1 (2002): 36-49. https://www.researchgate.net/profile/Albert-Segars-2/publication/220079710_An_Empirical_Examination_of_the_Concern_for_Information_Privacy_Instrument/links/5be32f36299bf1124fc2da16/An-Empirical-Examination-of-the-Concern-for-Information-Privacy-Instrument.pdf
Vaidya, Jaideep, and Chris Clifton. "Privacy-preserving k-means clustering over vertically partitioned data." Proceedings of the ninth ACM SIGKDD international conference on Knowledge discovery and data mining. 2003. https://www.cerias.purdue.edu/assets/pdf/bibtex_archive/2003-47.pdf
Lo Piano, S. (2020). Ethical principles in machine learning and artificial intelligence: cases from the field and possible ways forward. Humanities and Social Sciences Communications, 7(1), 1–7. https://doi.org/10.1057/s41599-020-0501-9 https://www.nature.com/articles/s41599-020-0501-9.pdf
Choquette-Choo, Christopher A., et al. "Label-only membership inference attacks." International Conference on Machine Learning. PMLR, 2021. https://arxiv.org/pdf/2007.14321.pdf
Kifer, Daniel, and Ashwin Machanavajjhala. "Pufferfish: A framework for mathematical privacy definitions." ACM Transactions on Database Systems (TODS) 39.1 (2014): 1-36. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.436.2576&rep=rep1&type=pdf
Damien Desfontaines, and Bal´azs Pej´o, "SoK: Differential Privacies A taxonomy of differential privacy variants and extensions", 2019. https://arxiv.org/pdf/1906.01337.pdf
Josh Smith, et al. "Making the Most of Parallel Composition in Differential Privacy", Privacy Enchancing Technologies Symposium (PETS) 2022. https://petsymposium.org/2022/files/papers/issue1/popets-2022-0013.pdf
6月
Cormode, Graham, et al. "Empirical privacy and empirical utility of anonymized data." 2013 IEEE 29th International Conference on Data Engineering Workshops (ICDEW). IEEE, 2013. http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.591.8092&rep=rep1&type=pdf
小栗秀暢. "プライバシー保護データ流通のための匿名化手法." システム/制御/情報 63.2 (2019): 51-57. https://www.jstage.jst.go.jp/article/isciesci/63/2/63_51/_pdf
高橋翼. 系列データの匿名化に関する研究. Diss. 筑波大学 (University of Tsukuba), 2014. https://core.ac.uk/download/pdf/56657868.pdf
Ayala-Rivera, Vanessa, et al. "A systematic comparison and evaluation of k-anonymization algorithms for practitioners." Transactions on data privacy 7.3 (2014): 337-370. https://researchrepository.ucd.ie/handle/10197/9109
Dwork, Cynthia, et al. "Calibrating noise to sensitivity in private data analysis." Theory of cryptography conference. Springer, Berlin, Heidelberg, 2006. https://link.springer.com/content/pdf/10.1007/11681878_14.pdf
Nicholas Carlini, et al. "(Certified!!) Adversarial Robustness for Free!" arXiv preprint arXiv:2206.10550 (2022). https://arxiv.org/pdf/2206.10550.pdf
7月
U.S. Department of Commerce (1978), Statistical Policy Working Paper 2: Report on Statistical Disclosure and DisclosureAvoidance Techniques, U.S. Government Printing Office, Washington, DC. https://nces.ed.gov/fcsm/pdf/spwp2.pdf
Kellaris, Georgios, et al. "Differentially private event sequences over infinite streams." Proceedings of the VLDB Endowment 7.12 (2014): 1155-1166. http://people.csail.mit.edu/stavrosp/papers/vldb2014/VLDB14_WDP.pdf
書籍
- 漫画を含めた書籍:
29冊(前年比-34冊※)
※今年から雑誌は含めないことにした
技術書
- なし
ビジネス書・趣味
- 映画を早送りで観る人たち~ファスト映画・ネタバレ――コンテンツ消費の現在形~ (光文社新書)
- オルレアンの少女 (岩波文庫 赤 410-10)
- ジャンヌ・ダルク 超異端の聖女 (講談社学術文庫)
- プロジェクト・ヘイル・メアリー 上
- プロジェクト・ヘイル・メアリー 下
- 人間ぎらい (新潮文庫)
- 令和2年改正 個人情報保護法の実務対応-Q&Aと事例-
記事
昨年に引き続き、あまり記事を読んでいない。ただし、英語記事に目を通すようになった。 以下は今年読んでよかった記事。
- ブルシットプロダクトからチームを守れ! 「顧客が本当に必要だったもの」をいかに追求しつづけるか /bullshit product rsgt2022 - Speaker Deck
- インシデントレスポンスを自動化で支援する - Slack Bot で人機一体なセキュリティ対策を実現する | CloudNative Days Tokyo 2021
- さようなら、謎の数値ズレ。dbtを活用してデータ品質管理をはじめよう | by Sotaro Tanaka | Medium
- 「売れない営業の11の特徴」は売れる営業への道標|野村修平|note
- 不況下の事業計画の見直し - 攻めるべきスタートアップ、守るべきスタートアップ|原健一郎 | Kenichiro Hara|note
- HTTP 関連 RFC が大量に出た話と 3 行まとめ | blog.jxck.io
- 差分プライバシーによるデータ活用最前線 - Speaker Deck
- 死なないために - 宮田昇始のブログ
- sigstoreによるコンテナイメージやソフトウェアの署名 - knqyf263's blog
- 世界中のITエンジニアが悩まされている原因不明でテストが失敗する「フレイキーテスト」問題。対策の最新動向をJenkins作者の川口氏が解説(前編)。DevOps Days Tokyo 2022 - Publickey
- HPKE とは何か | blog.jxck.io
- 不況下での財務的な経営の舵取りについて|SatoshiYamada|note
- みずほ銀行システム障害に学ぶ | 川口耕介のブログ
- ソフトウェアエンジニアとしての姿勢と心構え / Software Engineer's Survival Guide - Speaker Deck
- 機械学習でハタラクをバクラクにするために LayerX に入社しました #LayerX|yu-ya4|note
- XMLHttpRequest とはなんだったのか | blog.jxck.io
- なぜETLではなくELTが流行ってきたのか - Qiita
- 生成AIが創れる世界|やまかず|note
Github
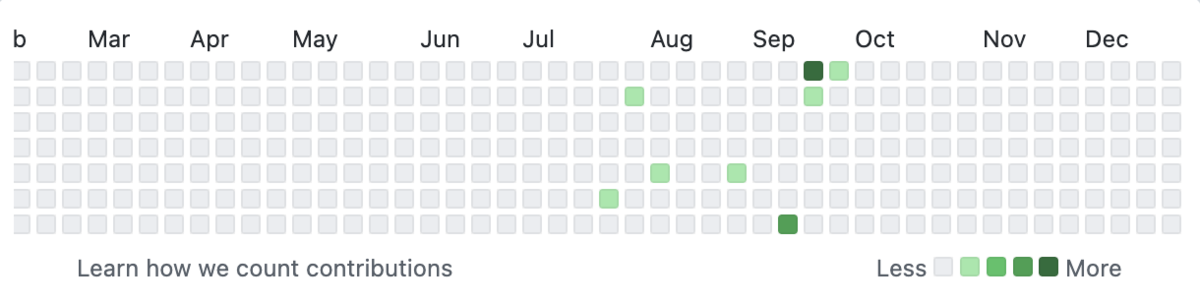
昨年の1,249 contributionsに対して、-1,231となった。
Githubで管理していないコードやクエリを書く機会が多かったため。
Scrapbox
1376→1611pages